My Store
Dstike Deauther Watch V4S
Dstike Deauther Watch V4S
Couldn't load pickup availability
Introducing the Dstike Deauther Watch V4S - a cutting-edge wearable that empowers you to delve into the world of cybersecurity. With capabilities for deauther attacks and bad USB attacks, this watch serves as your ultimate learning platform. Be more dangerous than ever with full support for Ducky scripts. If you know, you know. If you don't, learn. Explore its vast potential with access to comprehensive source code stored on the SD card. Dive into the realm of hacking with confidence and curiosity. Elevate your knowledge and skills as you unlock the possibilities. Experience the future of cybersecurity firsthand.
What's new in the V4S?
- Micro USB -> Type-C USB
- Power supply updated (Press and hold for 3 seconds to power on/off.)
- SD slot added
- Fully support Ducky Script
- ESP07S(1M)->ESP07(4M)
Function
- Deauther Attack: Disconnect 2.4G WiFi
- Deauther Beacon: Create fake networks
- Deauther Probe: Confuse WiFi trackers
- Packet Monitor: Display WiFi traffic
- Clock: Real Time Clock Adjustable
- Bad USB Attack: The Human Interface Device (HID) Attack
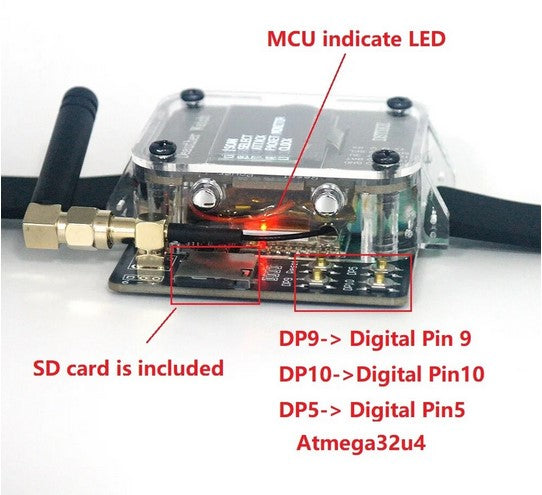
Package Included
- 1x Deauther Watch V4S
- 1x TypeC Power Cable
- 1x Arcylic Cover Board
- 1x SoftWare Manual
More Info
Deauth
The deauthentication feature is designed to close the connection of WiFi devices by sending deauthentication frames to the selected access points and client devices. It's important to note that this attack is only possible because many devices do not implement the 802.11w-2009 standard, which provides protection against such attacks.
To ensure proper usage, please select only one target at a time. If you select multiple targets running on different channels and initiate the attack, the system will rapidly switch between those channels, making it difficult to reconnect to the access point hosting the web interface.
Beacon
Beacon packets are used to advertise access points. By continuously sending beacon packets out, it will look like you created new WiFi networks. You can specify the network names under SSIDs.
Probe
Probe requests are sent by client devices to ask if a known network is nearby. Use this attack to confuse WiFi trackers by asking for networks that you specified in the SSID list. It's unlikely you will see any impact by this attack with your home network.
Bad USB
A HID (Human Interface Device) attack is a type of cyberattack that leverages a device, often designed to mimic a keyboard or mouse, to exploit vulnerabilities in a computer system or network. This attack method takes advantage of the fact that most computer systems inherently trust input from HID devices, such as keyboards and mice.
Share